How Do HID® Cards Work?
HID® cards, commonly used for access control systems, operate based on a technology that enables individuals to be securely identified and able to authenticate themselves.
HID cards typically contain a microchip and an antenna. The microchip stores the card's unique identification number, while the antenna allows the card to communicate with card readers.
There are various types of HID cards, including proximity cards, smart cards, and magnetic stripe cards. Proximity cards operate at a short range and use radio frequency identification (RFID) technology, while smart cards may have additional functionalities, such as storing encrypted data.
When a user presents an HID card to a reader, the following steps occur:
Activation: The card reader emits a radio frequency signal, activating the card's antenna.
Data Transmission: The card responds by transmitting its unique ID number back to the reader.
Verification: The reader sends this ID to an access control system, which checks it against a database of authorized users.
Access Decision: If the ID is recognized and valid, the system grants access, often by unlocking a door or allowing entry to a secure area.
List of Common HID Formats
HID cards come in various formats, offering different levels of security and data capacity for access control systems. Below is a breakdown of common HID formats:
- 12 Bit: CASI F/2F 12 Digit Magstripe, used in older systems.
- 13 Bit: MIDAS, often for legacy systems.
- 15-27 Bit: These include TECOM, Standard 26-bit (H10301), INDALA 26-bit, and variations like 27-bit formats, commonly used in commercial systems.
- 28-32 Bit: Includes formats like 32-bit HID, Wiegand, and INDALA, often used in corporate environments requiring moderate data storage.
- 33-36 Bit: Formats like HID 33-bit (D10202) and 35-bit Corporate 1000 offer higher security and greater data range.
- 37-40 Bit: HID 37-bit formats (H10302, H10304) and 40-bit Honeywell are widely adopted for enterprise-level systems requiring more sophisticated control.
- 42-56 Bit: Used by larger organizations, these include 56-bit Inner Range and TWIC/CAC for high-security systems.
- 64-128 Bit: TWIC/CAC 64-bit and PIV-I 128-bit are advanced formats used in government and high-security environments.
- 200-245 Bit: FASC-N formats offer extremely high security, often for federal systems.
These formats vary in data capacity and are chosen based on specific access control needs, offering flexibility for security and customization.
How to Determine HID Card Format
To determine what kind of HID door access card you need, follow these steps:
-
Check the Card Technology:
The most common technologies are HID iClass® and HID Proximity cards. Look for identifying marks like “HID Prox” or “iClass” on the card itself, which helps distinguish proximity cards from high-frequency cards like iClass®.
-
Check the Last Box of Cards
If you have the box from the last card order, look at the label for details like card format, facility or site code, and starting card number. These are typically preprogrammed, and you will want to avoid ordering a duplicate card number. Many control systems accept the standard 26-bit format (H10301), but others may require a proprietary or open format.
-
Inspect the Existing Cards
On existing cards, the site code and serial number may be printed. This doesn’t always tell you the format, but it provides clues. You may see numbers like 0009P or 0006L for proximity technology or the iClass® logo for iClass cards.
-
Ask for a Sample Card
Reach out to a card supplier and request a sample card, often in the standard 26-bit format, with a random site code and card number to test with your system.
-
Send in a Working Card
If you’re unsure, send a working card to a vendor like Easy Badges, who can read the card information and help determine the correct Wiegand format, site code, and programming.
-
Log into Your Access Control System
If you have access to the control system, you may be able to see the card format, facility code, and enrolled card numbers directly.
By following these steps, you can ensure you're ordering the right card for your system, avoiding duplicates, and ensuring proper programming.
HID H10301 Format
The HID H10301 format, also known as the standard 26-bit format, is one of the most commonly used prox card formats in access control systems.
It has a total of 26 bits of data, with 8 bits assigned to the facility code (which identifies the location or building) and 16 bits for the card number (which identifies the individual user). This encoding enables organizations to increase card security, as only those familiar with the format and facility code can interpret the information within the card.
This format allows for 65,536 unique card numbers and 256 possible facility codes. It's widely used because of its simplicity and broad compatibility with various access control systems.
Importantly, anyone can buy HID cards, but understanding the specific format allows for better implementation in control systems that accept the standard 26-bit format.
Within the HID H10301 format, there exist higher bit formats, such as 35 bit and 40 bit, which provide additional security features. However, one exception is the HID 37 bit format, which does not adhere strictly to the standard 26-bit format.
Wanna Save More on Your Access Control System? Get Free H10301 Format Cards
Looking to upgrade or set up your access control system with more affortable H10301 Prox cards?
We’ve got you covered! For a limited time, we’re offering FREE H10301 Format Prox Cards to help you get started.
No strings attached—just high-quality, industry-standard 26-bit H10301 cards ready for your system.
Get Your FREE H10301 Cards Now!
The Standard 26-Bit Wiegand Format
The Standard 26 Bit Format is a widely used representation for encoding information in digital systems, particularly in the context of access control and identification systems. Originally developed for use in proximity card systems and RFID technology, this format has become a popular choice due to its balance of simplicity and effectiveness.
The Standard 26 Bit Format consists of a total of 26 bits, which are typically divided into three main sections: the facility code, the identifier, and the parity bits.
1. Facility Code (Bits 1-8):
This section allows for the organization of different groups or facilities, making it easier to manage and identify multiple users or locations. The facility code can range from 0 to 255, allowing for 256 unique facilities.
2. Identifier (Bits 9-24):
This section provides a unique identifier for each card or user within a facility. It typically consists of 16 bits, allowing for 65,536 unique identifiers within the same facility code. This ensures that each card can be uniquely recognized by the system.
3. Parity Bits (Bits 25-26):
The last two bits are used for error checking through parity. They help ensure the integrity of the data being transmitted and can indicate whether the data has been altered or corrupted.
The Standard 26 Bit Format is primarily used in:
- Access Control Systems: Commonly found in security systems for buildings, offices, and other restricted areas, allowing for controlled entry based on user credentials.
- Time and Attendance Systems: Used for tracking employee attendance and managing workforce data.
- Identification Systems: Employed in various identification applications, such as employee badges, membership cards, and visitor management.
What Is HID® iClass®?
HID iClass® is a type of smart card technology used for secure access control systems.
Unlike traditional proximity cards, iClass® cards use high-frequency radio waves (13.56 MHz) for communication between the card and the reader, offering enhanced security.
iClass® cards can store additional data beyond just access control, such as encryption keys or biometric information. This makes them ideal for environments that require more than just basic access control, offering multi-functionality and improved protection against unauthorized duplication.
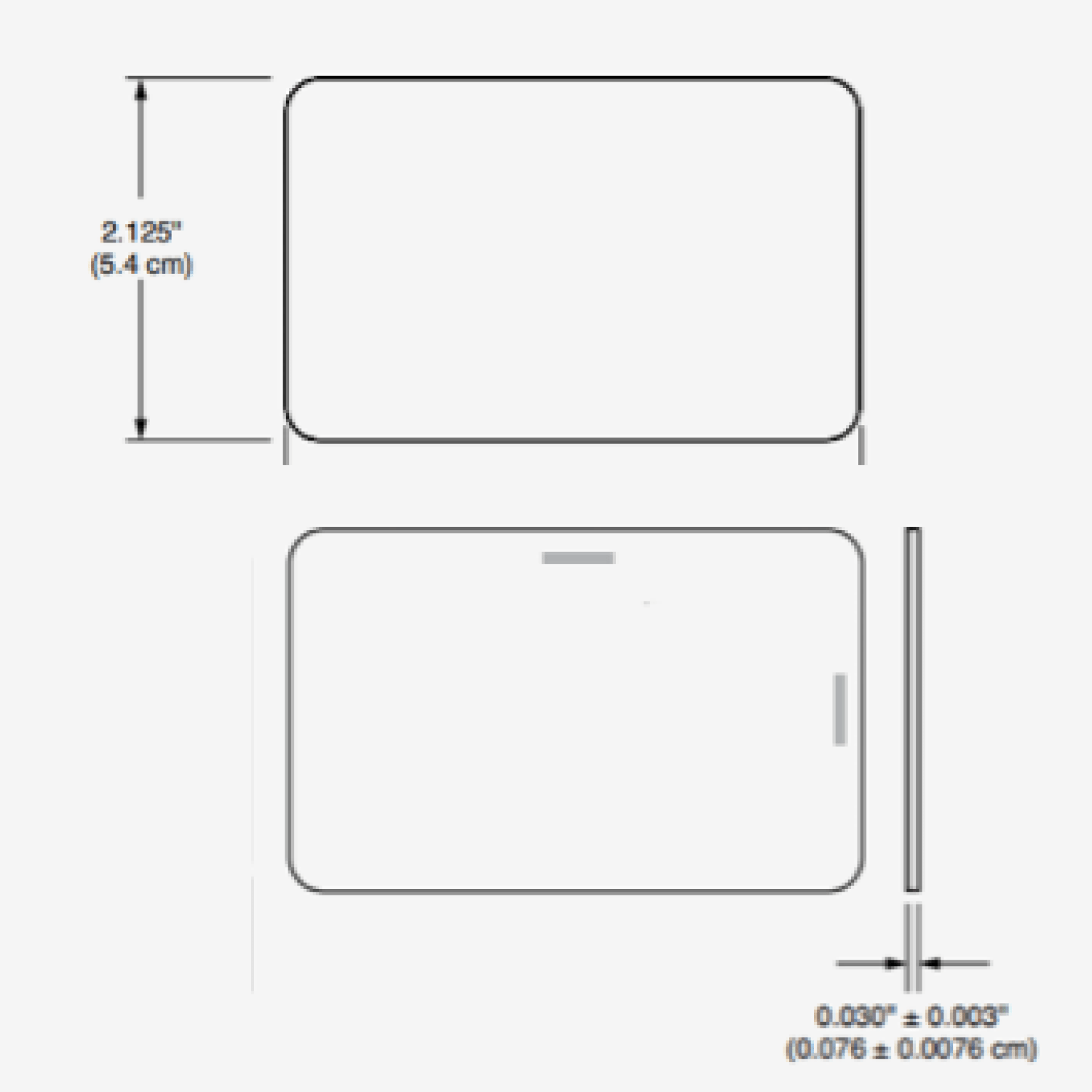
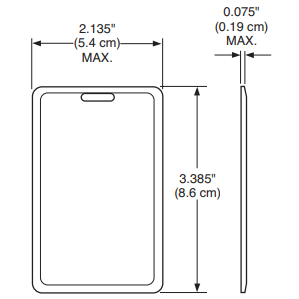
What Is A Clamshell Card?
A clamshell card is a type of access control card known for its durability and non-printable surface. These cards are thicker and sturdier compared to other types like printable proximity cards.
They are named “clamshell” because of their hard plastic outer shell, which protects the internal technology.
Clamshell cards are most commonly used in environments that prioritize durability over customization, making them suitable for high-traffic areas or rough handling situations.